There is almost no escaping email scams in this day and age. Everyone gets them. But, luckily after 50-odd years of emails existing, most of us know that there is no Prince with a fortune to bestow upon us so long as we first transfer a sum of money. Yet – as with anything, if there is an exploit to be found cybercriminals and grifters will make use. The complexity of email scams has only increased – some email scams can look incredibly authentic, while others are noticeably more amateur.
In this blog post, we’ll shed light on some common email scams targeting businesses, and provide some examples to help you recognise potential threats in your own inbox.
Common Email Scams Targeting Businesses
1. Fake Microsoft password reset requests
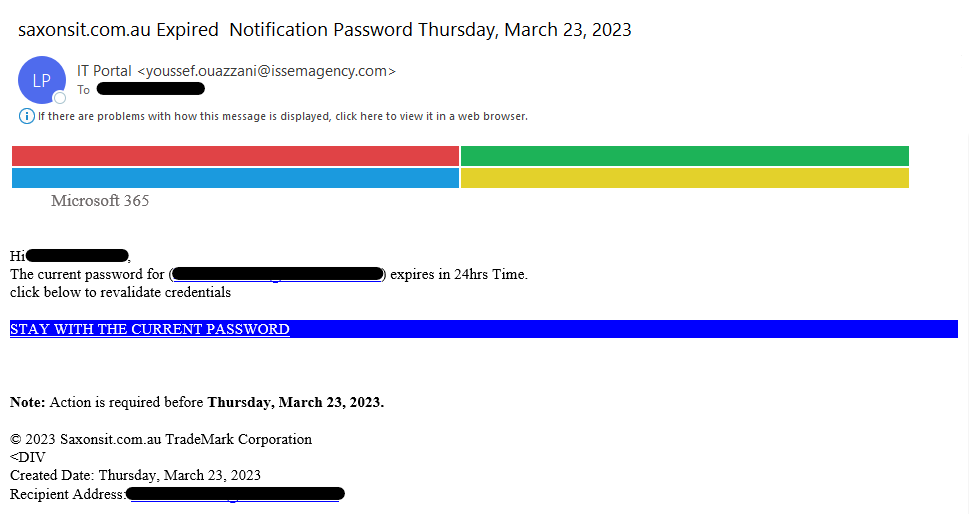
Microsoft will NEVER send you an email with a link requesting that you change your password. The quality of these scam emails can vary. Some may look just like other official emails you have received from Microsoft. The branding of the email may be convincing, and the wording clear. Below is an example of a more egregious attempt.
In this example, a staff member at Saxons IT received this scam email to their inbox. It was flagged as “to be reviewed” by our spam system. To begin with, this email has come from an unrecognised email address, with no relation to Microsoft. Additionally, the “TradeMark” at the bottom of the email is bazar, as Microsoft would have their own business details there, not the details of the company being emailed. Furthermore, the email layout itself is crude. The “Microsoft” logo is just a 2×2 table with the colours filled in (not the official Microsoft colours), which is why it looks stretched out as the table width is set to fill the screen. The font and layout are an additional giveaway. But remember, Microsoft never sends password reset emails, so that is your biggest giveaway!
2. Fake remittance advice and Invoice emails
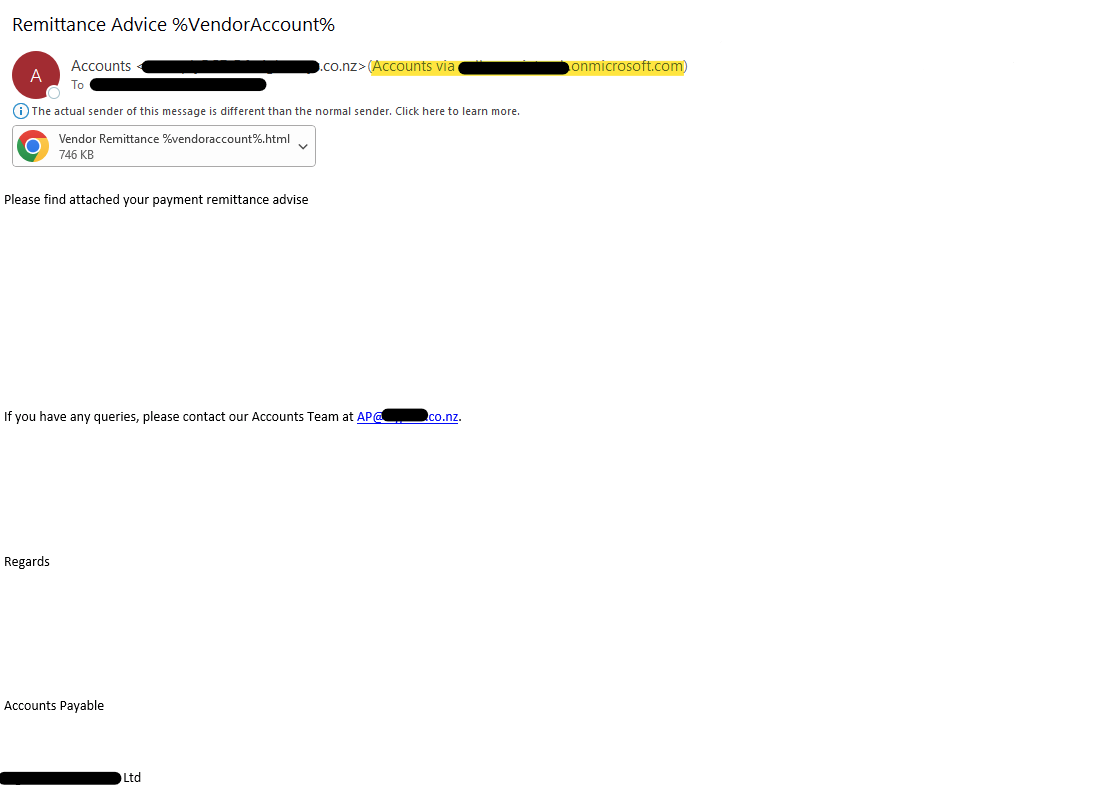
There has been an increase in fake remittance advice and invoice scams. These scam emails have cybercriminals pose as a real company, with a “remittance” or “invoice” attached. This attachment usually hides a link to a virus or other malicious item. In the below example, a scammer is attempting to impersonate the accounts department of a popular New Zealand freight company.
Highlighted in yellow, Outlook displays where the email actually came from. The “From” email was a spoof of the freight companies. You’ll also see that the attachment is actually a link, which usually contains malware or leads to a scam page. The spelling and grammar in this email are poor – “remittance advise“. Additionally, the “%” around words tends to indicate that the scammer intended to have the words between auto-filled with relevant information, but was unsuccessful in this case. But, the biggest giveaway that this was a scam to our finance team was… We have never interacted with this company before! But, in remittance scams, this is not always the case. If you are ever unsure about an email you have received from a vendor or client, reach out directly to a trusted contact via phone call to discuss further.
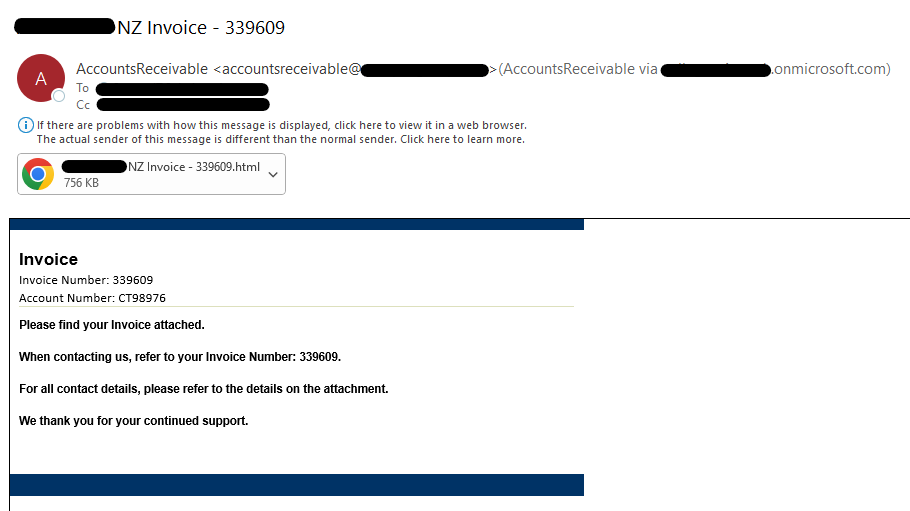
Here is an example of a fake invoice email scam, from the same scammer:
3. Fake voicemail notifications scams
Fake voicemail notification scam emails have been prevalent over the past couple of years. They prey on a business professional’s urgency to tend to a possible missed call. Interacting with these emails can lead to inadvertently compromising personal or corporate security.
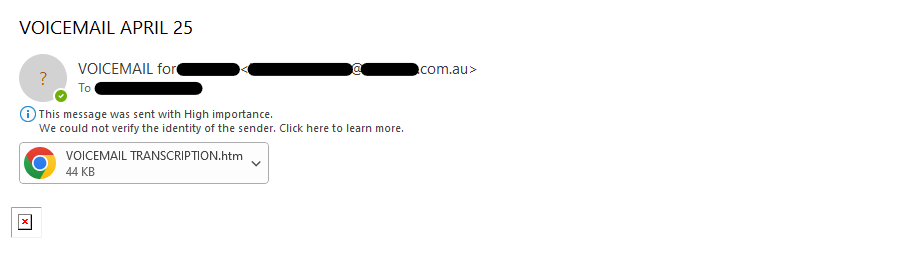
These email scams work by mimicking the legitimate voicemail notifications some companies have set up. This is where voicemails are sent to an employee’s email, allowing them to listen to the recording. The fake voicemail notification scams aim to lure recipients into clicking malicious links or downloading infected attachments.
Sometimes, the from email may even be your or another business email – this was the case in the example below. But, in this occurance, it was an act of domain impersonation and not the email itself being compromised. Most email applications will display what type of file is attached. Here you can see that it is a link – but when in doubt, always remember to hover before you click. This means that before clicking on any links or attachments, hover your mouse over them to preview the destination.
In conclusion, awareness is the first line of defense against email scams. By staying vigilant and informed, businesses can reduce the risk of falling victim to deceptive email practices and protect themselves from cybercriminals.