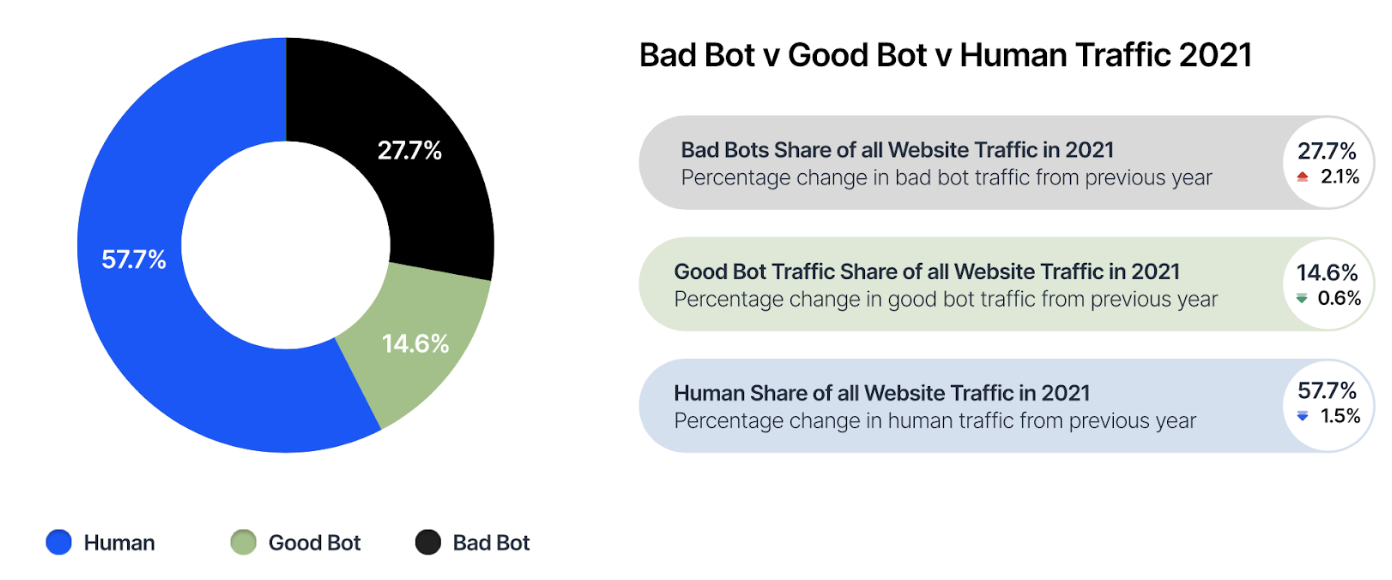
There are about the same amount of humans online as there are bots. In 2011, Imperva collated data for a study suggesting that 51% of Internet traffic was generated by non-humans. But what does that look like 10 years later? In 2022, Imperva’s Bot reports covering the 2021 period estimated that 42.3% of total web traffic consisted of online bots. At a glance this may seem like an improvement, but during the pandemic, some operators have experienced as much as a 60% increase in online traffic compared to before the crisis.
While bots have been a large part of the online ecosystem for over a decade, they are still often misunderstood by online users.
What are Online Bots?
A bot is a software program that runs automated tasks and operates on the Internet. Usually, bots are used to perform simple and repetitive tasks in a manner much faster than any human could. It should be noted that some online bots are “good”, while others are “bad” and used to launch malicious attacks.
Good Bots
Good bots are a critical part of the internets ecosystem, serving an important purpose. An example of this is a search engine spider – or “web crawler” – allowing internet search companies (such as Google) to analyse millions of files on servers throughout the world. Around 15% of total web traffic consists of these good bots.
Bad Bots
Bad bots are are malicious with their intent. Bots can prove to be quite persistent on their targets, presenting a challenge for businesses that want to maintain smooth operations. Bots can impact bandwidth consumption, thus effecting the experiences for a businesses legitimate customers visiting their site. OWASP, Open Web Application Security Project, detail an extensive list of automated threats bots present. Some of which include:
- Scraping data from sites without permission from site owners with the intent to reuse it to gain a competitive edge.
- Scalping stock from websites through automation, especially for limited availability items, and reselling them at a higher price.
- Creating distributed denial of service (DDoS) attacks targeted at networks or applications.
- Spamming website comments or emails with unsavoury comments and phishing links.
How do “Bad Bots” Operate?
Bad bots operate by attempting to interact with applications in the same way a legitimate human user would – masking themselves to avoid detection. This makes bots increasingly difficult to identify and block, especially with technology and bot methods advancing over the years. Through the nature of their automation, bots enable high-speed abuse, misuse, and attacks on websites, mobile apps, and APIs.
It’s important to remember that these malicious online bots do not act on their own, but are the product of “bot operators”. These bot operators can range from being antagonistic hobbyists that enjoy wreaking havoc, to immoral competitors wanting to gain an upper hand in their industry, to fraudsters utilising the online landscape to conduct their scams in mass.
Who is impacted by Bots?
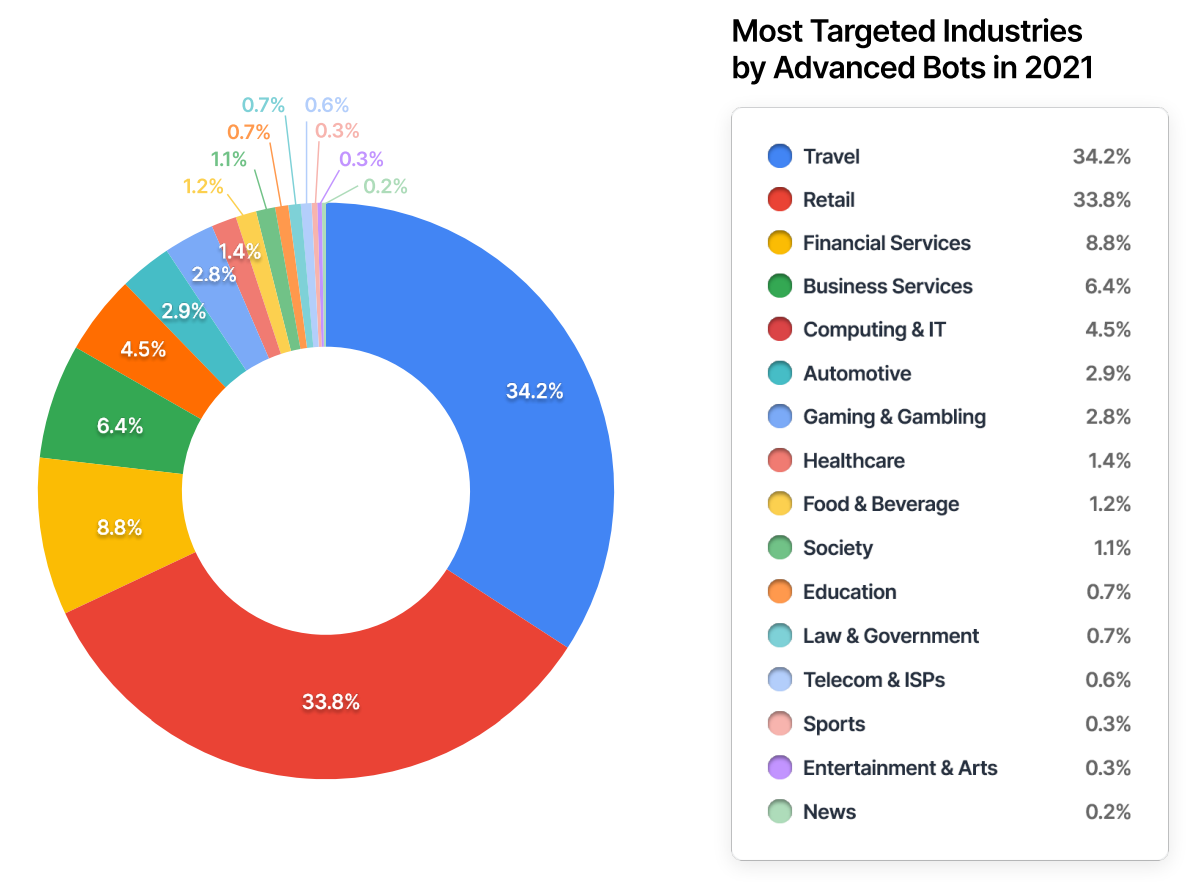
Every industry is impacted by bots in some form. The common attacks seen may differ from industry to industry, and ratios of simple, moderate, and advanced bots vary by industry. The below graph displays the most targeted industries by advanced bots. The distribution of advanced bot attacks across each industry provides a different perspective – revealing what industries had the the highest advanced bot targeting rates in the reporting period.
Of the top 5 most bot attacked countries, Australia comes in second with 6.8% of bad bots targeting the country. Although, the United States coming in first takes close to half of all malicious bot attacks world wide.
Top 5 Most Attacked Countries
- United States 43.1%
- Australia 6.8%
- United Kingdom 6.7%
- China 5.2%
- Brazil 3.3%