We’ve discussed many types of scams that you or your business may encounter, but here’s an uncomfortable one that can’t go ignored – sextortion. These email scams lean on being embarrassing, and rely on people’s doubt. While there are cases of sextortion where the cybercriminal has what they claim to have, we will be discussing the rise of bulk-sent sextortion email scams. These are baseless, empty threats.
Understanding Sextortion Scams
Sextortion scams typically begin with an email claiming that the sender has compromising or explicit content of the recipient, these emails often sent in bulk, and generic enough to apply to most individuals. The fraudulent message threatens to expose this content unless a ransom is paid, usually in Bitcoin.
How the Scam Operates
Intimidating Subject Lines:
Scammers use provocative subject lines to grab the attention of their recipients. These may include threats of exposing intimate photos or videos purportedly in the possession of the sender.
False Evidence:
The scammer claims to have compromising material and may include fabricated details to make the threat seem more convincing. This can include references to hacked passwords, websites visited, or personal information. Sometimes, the details are generic, such as claims to have seen you visiting illicit websites, without clarification.
Demands for Ransom:
The scammer demands a ransom, typically in cryptocurrency, in exchange for their silence. Typically, there is a deadline in the email, which can cause panic and confusion for victims. The urgency of the situation is emphasised to pressure the victim into immediate compliance, without further thought.
Examples of a Fake Sextortion Scam Email
Below are two examples of fake sextortion email scams from 2023. These examples show generic sextortion emails, where there is no unique data in the body of the emails, such as the receiver name, business details, or personal identifying information. You’ll find both emails are similar in structure.
Reader discretion is advised.
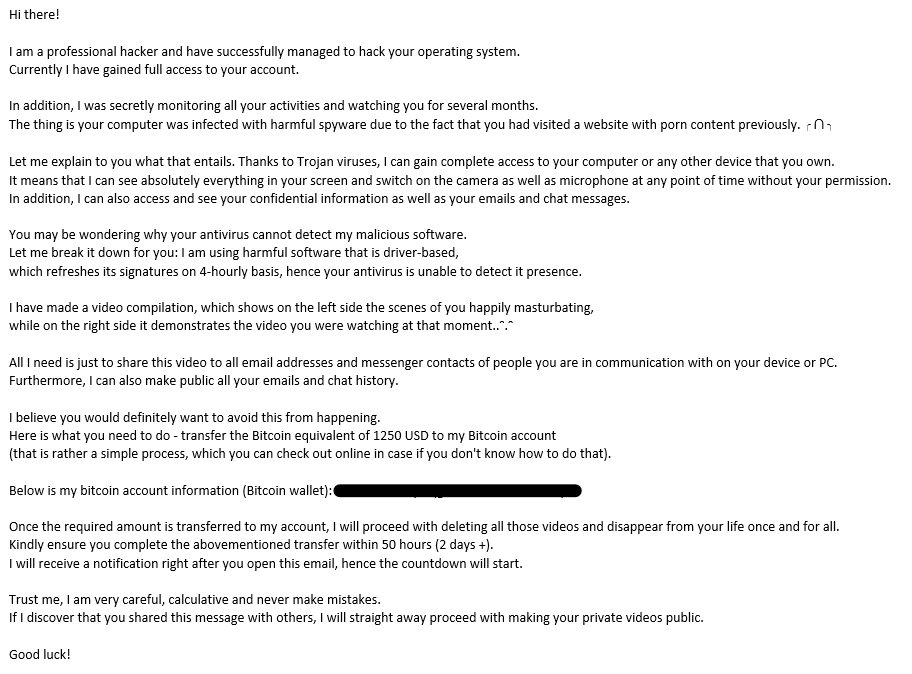
EXAMPLE 1
Subject: Your personal data has leaked due to suspected harmful activities.
Body:
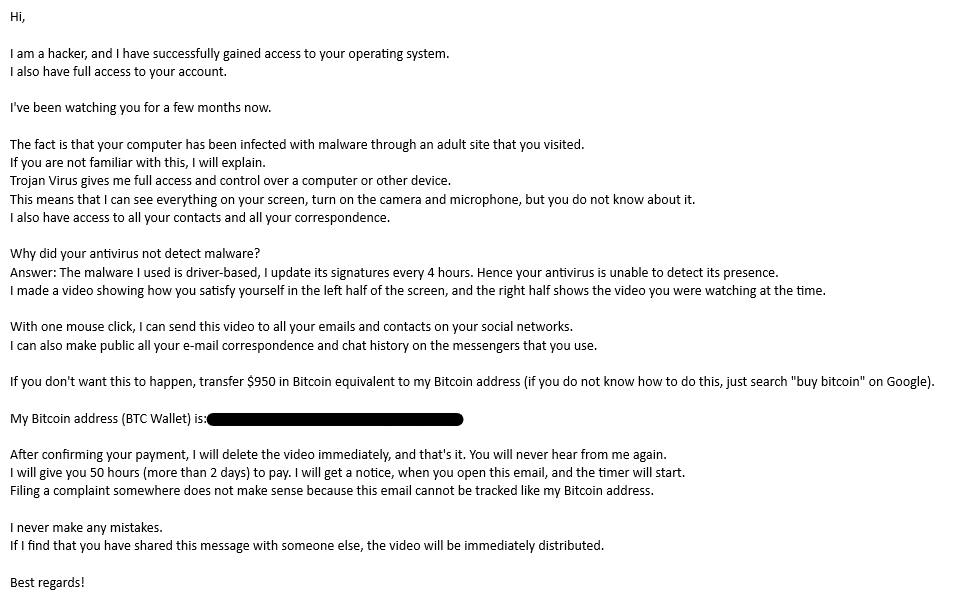
EXAMPLE 2
Subject: Your account is hacked. Your data is stolen. Learn how to regain access
Body:
Protecting Yourself from Sextortion Scams
1. Maintain Calm and Skepticism:
Take a moment to breathe and analyse the situation. Scammers rely on fear and panic to manipulate their victims. Avoid making impulsive decisions.
2. Do Not Respond or Pay:
Under no circumstances should you respond to the scam email or pay the ransom. Engaging with the scammer only encourages further exploitation.
3. Verify Claims:
Check the claims made in the email. Cybercriminals often use generic information obtained from data breaches, sometimes there is no information relating to the receiver at all. If the details seem dubious, they likely are.
4. Secure Online Accounts:
Strengthen your online security by updating passwords, enabling two-factor authentication if it isn’t already, and monitoring your accounts for unusual activities.
5. Educate Others:
Share information about sextortion scams with friends, family, and colleagues. Awareness is a powerful tool in preventing these scams from succeeding. They exist because they work.
6. Speak to Your IT People:
Whenever you have any issues or concerns regarding your emails, reach out to your IT department or IT services provider. They will be able to investigate the email further, and give you some peace of mind.
By understanding the tactics employed by scammers and adopting proactive measures, you can protect yourself and others from falling victim to these malicious ploys.